|
There were many attempts during the period of the 1980s and early 1990s to slow the tide of software piracy, this article will highlight the need and function of these programs and devices. During the era of the home micro, the only way of getting data into the machines was through cassette tape and later through floppy disk, firstly 5.25 and then 3.5 inch disks. Cassettes were easy to copy for anyone with a tape to tape system, and it was very common for children in the playground to be offering a C90 tape full of programs to fellow classmates. Floppy disk versions of games were not safe either, as programs were being created all the time that would bypass any on disk security, and produce new copies. Hyper Loader This was a faster loading programme used by companies such as Ocean and Ultimate. Not only did the player spend less time waiting for the program to load, the higher pitch noise would mean that copying the tape from one to another degraded the signal to a point the game might not load. Code Sheets This was a simple means of trying to stop a game being copied, a sheet with a huge grid The main problem with this was, if the player was patient enough, they could copy the whole sheet by hand, or pop down to the local newsagent or library and get a copy of the sheet. This was of course was long before having printers and scanners in the home.
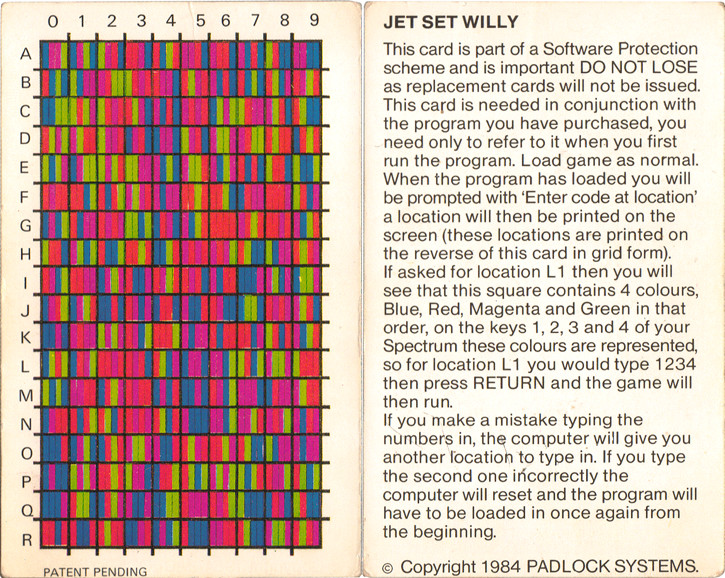
Jet Set Willy Code Card This was a small piece of card that required the player to input four colours matching to a chart with a letter up the left hand side, and a number along the top. We have a page for the card here. http://www.computinghistory.org.uk/det/57256/Jet-Set-Willy-Code-Card/ Lenslock This was a plastic device that was held onto the TV screen to read a code needed to start the game, unfortunately seriously flawed in that it needed a certain size TV to work, and was very fiddly to use, we have a page dedicated to Lenslok here. http://www.computinghistory.org.uk/det/56946/Lenslok-Software-Protection-Device/ Manual Protection A nice simple form of protection was by using the manual in the box, this was far harder to get around, it would give you for example, a page number, the paragraph, and then the 5th word in the paragraph. The idea was that the player was unlikley to be able to copy the whole manual, especially for a game of great complexity with a large booklet, and also the person they had borrowed the game from was not going to want the manual damaged. The Code Wheel This is a cardboard or plastic wheel supplied with the game, which the player would use to access the game, by matching symbols or numbers to get a code number. We have a code wheel page here http://www.computinghistory.org.uk/det/57263/Code-Wheel/ Dongle During the 16 bit era, companies like Ocean would produce a little electronic board that would plug into the mouse port as the game loaded. If the dongle was not present, the game would not load. When the game was re-released on a budget label, the dongle would be replaced by manual protection to save costs. Dark Manual Protection Knowing full well that a normal code sheet or manual could be copied easily, some software companies would use a dark table, the numbers were put on a black background, while being a slightly lighter shade of black themselves, this would stop the photocopier of the day from producing a useable copy. On Disk Protection schemes Their were various attempts to make disks hard to copy, one of the usual ways was to have a separate piece of code in the disks header, that normal copying would not take onto the new disk, so the game would not run, unfortunately, there were hackers who could crack these problems, proudly demonstrating their skills on flashy screens after the game loaded, and before it ran. The impact of any of these methods on software being copied is hard to measure, but they are an interesting part of history, many of the game files being used in emulators are hacked versions, so these efforts of the software companies in past times need to be preserved along with the software itself.
Date : Unknown This exhibit has a reference ID of CH57266. Please quote this reference ID in any communication with the Centre for Computing History. |
|
 of numbers. The game would load, and you would be given a number on screen, you would look down the list, and find the corresponding number alongside it, type that in and the game would run.
of numbers. The game would load, and you would be given a number on screen, you would look down the list, and find the corresponding number alongside it, type that in and the game would run.